HTTP protocol
Communication between the client and a server typically non-encrypted or plain text while we use HTTP protocol.
Pitfall
Any middle hacker can interrupt the connection between the client and server and manipulate the data as it involves no encryption.
How to overcome this ?
As the domain owner one can purchase a digital certificate from CA(Certificate Authority) who are considered as trusted.
A certificate will contain the Owner's name, public key , Issuer's(CA's) name,Issuer's(CA's) signature, domain details, expiry date etc .
After the SSL/Leaf certificate is associated with a domain,the communication between client and server will be encrypted. Now the HTTP will become HTTPs.
Note: Associating the SSL certificate means it enable the encryption between client and server but does not mean ,the domain owner will never misuse your personal information.
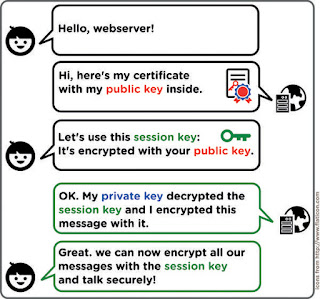
How does SSL work ?
Pitfall
There is a problem here. Let's assume that there is a hacker comes in the middle with his own custom certificate and private key.
In this case, The client does not know if it is really communicating with the real server but it keep responding to the hacker without realizing the fact.
How it can be resolved ?
One way to solve this problem is to have the client have a set of one or more certificates it trusts. If the certificate is not in the certificate chain, the server is not to be trusted.
A certificate chain can have SSL/Leaf certificate, one/more Intermediate certificates, Root certificate.
To understand more about Certificate chain, check the following references
https://mailapurvpandey.medium.com/ssl-pinning-in-android-90dddfa3e051
https://support.dnsimple.com/articles/what-is-ssl-certificate-chain/
https://www.ssldragon.com/blog/root-vs-intermediate-certificates/
Any certificate that sits between the Leaf/SSL Certificate and the Root Certificate is called a chain or Intermediate Certificate. The Root CA Certificate is the signer/issuer of the Intermediate Certificate. The Intermediate Certificate is the signer/issuer of the SSL Certificate.
The server fetches the SSL chain of trust for client, so that the client will verify if one or more certificates in the app\res folder matches with the each certificates in the set.
If one of the certificate does not match with the certificates in chain, then it will break the chain and throw an exception.There are several downsides to this simple approach. Servers should be able to upgrade to stronger keys over time ("key rotation"), which replaces the public key in the certificate with a new one. Unfortunately, now the client app has to be updated due to what is essentially a server configuration change.This is especially problematic if the server is not under the app developer's control, for example if it is a third party web service.This approach also has issues if the app has to talk to arbitrary servers such as a web browser or email app.
In order to address these downsides, servers are typically configured with certificates from well known issuers called Certificate Authorities (CAs). The host platform generally contains a list of well known CAs that it trusts. As of Android 7.0 (Nougat), Android currently contains over 100 CAs that are updated in each release and do not change from device to device. Similar to a server, a CA has a certificate and a private key. When issuing a certificate for a server, the CA signs the server certificate using its private key. The client can then verify that the server has a certificate issued by a CA known to the platform.
However, while solving some problems, using CAs introduces another. Because the CA issues certificates for many servers, you still need some way to make sure you are talking to the server you want. To address this, the certificate issued by the CA identifies the server either with a specific name such as gmail.com or a wildcarded set of hosts such as *.google.com.
Learn the following
1. What are the scenarios we need a custom certificate rather than embedded root certificate?
2. How to provide domain configuration with domain name, certificates associate with a domain etc ?
3. How to add additional CAs with default root CAs ?
4. Much more....
Please check the official page https://developer.android.com/training/articles/security-config
Also check the ways for SSL pinning at https://mailapurvpandey.medium.com/ssl-pinning-in-android-90dddfa3e051

Comments
Post a Comment